Key Insights to Know Before Starting Packet Capture
*This article is an English translation of the Engineer Notes article as of Mar 14, 2022.
*Please note that the content may have been updated since then.
Our product, SYNESIS, is a packet capture device. Its key feature is the ability to store large volumes of packets without any loss over extended periods.
Packet capture is a legacy technology that has been around for a long time, but it is still widely used today as a standard method for visualizing networks, employed by engineers of all levels from novices to veterans. In this article, I will share some insights that I wish I had known before I started working with packet capture as a rookie engineer.
Table of Contents
Information Contained in Captured Packets
Things to Know Before Capturing Packets
Pcapng Extended Fields for Adding Information
Important Considerations for Captured Data
What is Packet Capture?
Packet capture refers to the process of receiving a copy of communication packets through some method and writing them to memory or a hard disk.
This "some method" typically involves using TAP or SPAN. For more details, please refer to our article TAP vs. SPAN: Choosing the Right Tool for Network Packet Capture. These methods allow you to capture packets without affecting the network.
While it is also possible to capture packets by participating in the network without using SPAN or TAP, in such cases, your own communication packets are included in the captured data. This should be considered during analysis.
Information Contained in Captured Packets
Here is a screenshot of a Pcap file opened in Wireshark.

Let’s break down the information in these captured packets using the 5W1H framework.
| 5W1H | Information |
|---|---|
| When | Although packets themselves do not contain time information, the capture file includes the "time information from the capturing device." |
| Where | Packets do not contain information about where they were captured. You need to manually track the location information. |
| Who | Packets contain MAC addresses and IP addresses. |
| What | Packets contain information about protocols and payloads. |
| Why | (Obviously) The reason for packet capture is not contained in the packets. |
| How | The method of packet capture is not included in the packets. |
This means that some important information is not included in the captured packets. Therefore, when saving captured data, it is necessary to keep a record of where the data was captured and how it was captured (e.g., capture method, filter settings, and devices used for capturing).
Things to Know Before Capturing Packets
Packet capture is a highly effective tool for understanding network conditions, but it won't reveal everything happening on the network. With that in mind, here are some important points to consider before you start capturing packets.
- The most important thing in packet capture is to determine your "goal." You need to clarify why you are capturing packets before you begin.
- While packet capture is useful, it is not omnipotent. Packet capture only provides information about the packets flowing at the capture point. Therefore, it is crucial to determine the capture point. If the target communication cannot be captured, you need to consider whether it is even flowing at that point, based on the network configuration. Additionally, it may be necessary to change the capture point. Be aware that the appearance of packets may differ depending on the capture method.
- Packet capture data alone is not sufficient. You need to know where and how the data was captured. This is particularly important if the person capturing the data is different from the person analyzing it. In such cases, you need to communicate not only the capture data but also the capture information (e.g., capture point, method, and filters) to the analyst.
- Packets do not contain time information. The time information is provided by the capturing device. Therefore, you need to synchronize the time of the capture device with the network devices in advance. If long-term capture is required, choose a dedicated capture device that can synchronize time during capture.
- There are many preparations to be made before starting the capture process. In addition to determining capture points, methods, and time synchronization as mentioned above, you should also check network utilization rates, select the capture device, decide on how to record data, establish file naming conventions, and choose analysis tools. Planning these aspects in advance will help ensure smooth capture operations on-site.
Pcapng Extended Fields for Adding Information
Pcapng is a file format that was added with the later versions of Wireshark 1.x. It has various improvements over the traditional Pcap file format, one of which is the ability to extend fields.
Using this feature, you can add information such as capture location and method to the captured packet data. The following three points are particularly useful to remember.
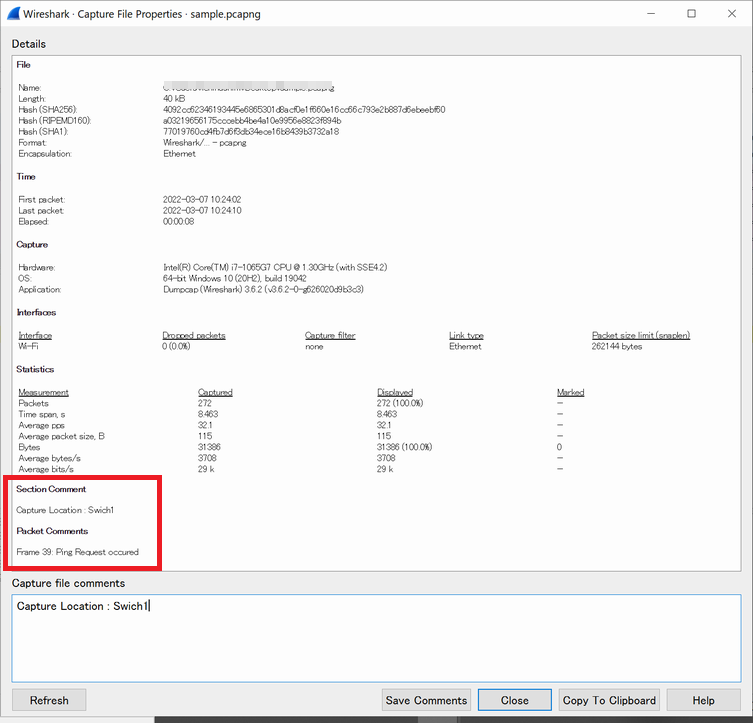
1. Capture File Comment Function
You can add comments to the entire file.
Select [Statistics] menu > Capture File Properties, enter your comments in "Capture file comments," and click "Save Comments."
You can use this function to add information such as capture points.
2. Frame-by-Frame Comment Function
You can also add comments to individual frames.
Right-click on the "Packet List" and select Packet Comments > Add New Comment... to add comments.
Incidentally, in my environment, entering comments in Japanese caused garbled text, even when Wireshark was set to display in Japanese. Therefore, it might be best to avoid using double-byte characters when entering comments.
3. How to Check Comments
You can view comment information by selecting [Statistics] menu > Capture File Properties.
Also, don't forget to save the file after editing any comments on the file or packets.
Important Considerations for Captured Data
Captured data contains a wealth of detailed information, including the source and destination IP addresses, MAC addresses, protocols used, and even parts of the communication itself. For instance, by analyzing a specific packet, one can determine who is communicating with whom, what services are being used, and sometimes even part of the transmitted data. This level of detail requires careful handling and management.
It’s crucial to enforce strict access controls and grant only the minimum necessary permissions. Additionally, setting a retention period for stored data is essential. Long-term storage increases the risk of data leakage, so unnecessary data should be deleted to ensure efficient data management.
Choosing a Packet Capture Product
Choosing the right packet capture product is essential for capturing packets without any loss. Sometimes, it’s hard to tell if packets aren't flowing on the network or if packet loss is due to the product's poor performance. That’s why it’s important to choose a product that ensures reliable capture.
Our company, with over 20 years of experience in packet capture technology, has developed and now offers "SYNESIS". SYNESISprovides the world’s highest continuous packet capture performance, backed by patents related to its capture technology.
If you would like a demonstration or PoC of SYNESIS, please feel free to contact us using the button below.
Afterword
It's been over 10 years since I’ve been deeply involved with packet capture products. While the architecture of packet capture itself hasn’t fundamentally changed, I feel that the data (protocols) and environments in which users are capturing have definitely evolved.

